IT security in hybrid working models
The future of work is hybrid. This paradigm shift is associated with numerous new requirements, be it the role of the office or the type of collaboration. IT departments are also facing new challenges as a result of the transformation to the hybrid working model. IT and data security will have to be rethought in the future.
What risks does hybrid working pose for information security?
For IT security, the shift to mobile working means ensuring a secure working environment outside the company office as well. Both technical and human vulnerabilities need to be taken into account.
Unsecured environments
Employees in remote work access company data from a wide variety of locations. They regularly switch between well-protected company networks and less well-secured, sometimes unencrypted home networks or public hotspots. Such unsecured Wi-Fi networks are usually an easy target for attackers to gain access to sensitive data. At the same time, this access makes it impossible for IT departments to identify suspicious activity based on IP addresses and prevent unauthorized access.
Non-protected end devices
In the home office, access is no longer only via the work computer. Instead, employees often use private devices, for example to check chat messages or emails on their smartphone or tablet. However, private devices are usually not under the control of the company. There is therefore often no adequate password protection or regular updates. Other devices registered on the same network also pose a potential risk.
Carelessness on the part of employees
How can organizations ensure IT security in the hybrid working model?
Modern mobile devices for employees

Allowing employees to work with outdated private technology that is not managed by the company entails high security risks. Instead, all colleagues should work with the latest technology and regularly updated software. This is not only recommended for security reasons, but also guarantees maximum productivity. The use of private devices is also problematic from a data protection perspective.
laptops, smartphones & tablets
Encrypted data transmission
Access management for employees
Another security precaution is the individual assignment of rights for individual users or user roles. With Single Sign On (SSO), access rights can be assigned or withdrawn with little effort. At the same time, the IT department always knows which employee has access to which data. For users, SSO offers the advantage of having access to all relevant applications and services with just one account.
To prevent identity theft, multi-factor authentication provides additional security when logging in. Multiple confirmation of your identity ensures that you are actually the person you claim to be.
Establishing a safety culture
In a hybrid working environment, the human factor will play an even more important role with regard to IT security in the future. Companies can reduce avoidable risks by providing targeted training on IT and data security, the secure use of end devices and the protection of personal data. This is because regular training sessions not only create an awareness of potential dangers, but also provide employees with the right tools to deal with the risks appropriately.
The following measures can already achieve an appropriate level of protection in the home office:
- Protect WLAN networks with a password
- Use secure, unique passwords for applications and services
- Perform regular updates
- Keep documents and devices inaccessible to unauthorized persons
Maintain full control with mobile device management
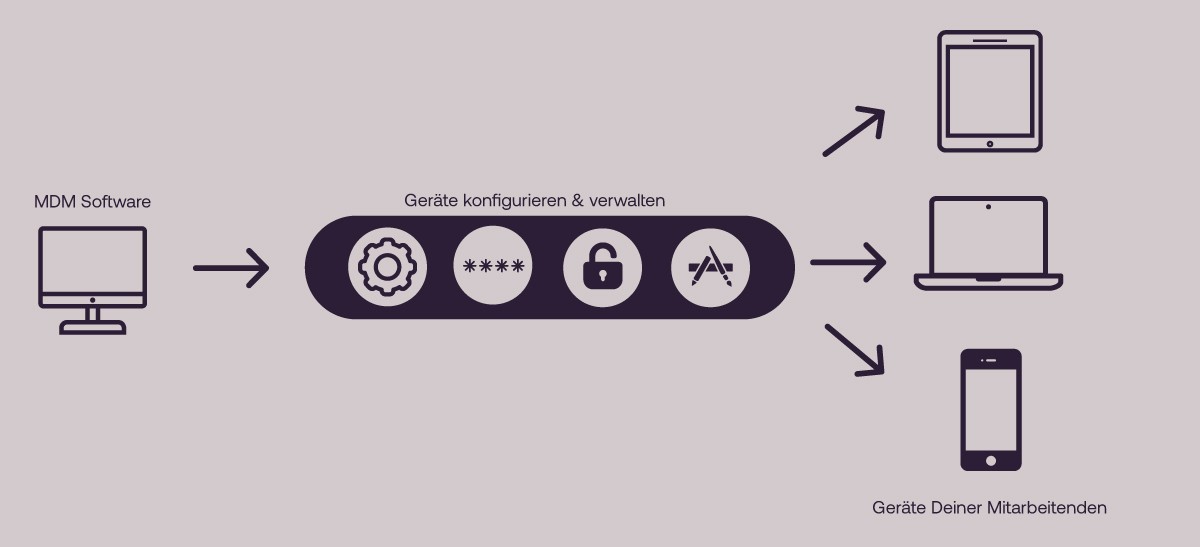
Mobile device management (MDM) is one way of implementing many of the measures mentioned above. This gives IT departments full visibility and control over all devices. Once the device has been registered once in the MDM software, it can then be easily managed, secured and monitored remotely from a central location. It doesn't matter whether they are company-owned or private devices.
A wide range of functions and configurations can be set up via the MDM software console. The features of an MDM solution include, for example
- Configuring network access
- Provision and updating of apps and applications
- Access management for individual users or roles
- Enforcement of security guidelines, such as password strength
- Device encryption
- Monitoring
- Inventory & Management
- White- & Blacklisting
- Deleting and locking the device remotely
- and much more
Mobile Device Management is part of our Device as a Service solution. We would be happy to advise and support you in setting up and configuring your individual MDM solution.
Here you can find out more about Device as a Service with Lendis.